How DePIN Networks Protect Against Cyber Threats. In today’s digital age, cybersecurity is of paramount importance. As cyber threats continue to evolve and become more sophisticated, traditional centralized networks are struggling to keep up with the increasing demands for security and privacy. Enter Decentralized Physical Infrastructure Networks (DePIN), a revolutionary approach to network security that leverages the principles of decentralization, cryptography, and blockchain technology. This blog explores how DePIN networks protect against cyber threats, offering enhanced security features and robust protection mechanisms.
Understanding DePIN Networks
Definition of DePIN Networks
DePIN Networks are decentralized infrastructures that utilize a combination of blockchain technology and physical devices to create secure, reliable, and transparent networks. Unlike traditional centralized networks, DePIN networks distribute data across multiple nodes, ensuring that no single point of failure can compromise the entire system.
How DePIN Differs from Traditional Networks
Traditional networks rely on centralized servers and infrastructure, making them vulnerable to single points of failure and targeted attacks. In contrast, DePIN networks spread data across numerous nodes, enhancing redundancy and security. This decentralized approach makes it significantly more challenging for attackers to compromise the entire network.
The Growing Cyber Threat Landscape
Overview of Common Cyber Threats
The cyber threat landscape is continuously evolving, with new threats emerging regularly. Some of the most common cyber threats include:
- Malware: Malicious software designed to damage or gain unauthorized access to computer systems.
- Phishing: Fraudulent attempts to obtain sensitive information by pretending to be a trustworthy entity.
- Ransomware: Malware that encrypts a victim’s data and demands payment for the decryption key.
- DDoS Attacks: Distributed Denial of Service attacks that overwhelm a network with traffic, rendering it inaccessible.
Statistics on the Increase in Cyber Attacks
Cyber attacks have been on the rise, with alarming statistics highlighting the growing threat:
- In 2020, the FBI reported a 300% increase in reported cybercrimes.
- Cybersecurity Ventures predicts that cybercrime will cost the world $10.5 trillion annually by 2025.
- A 2021 study found that 68% of business leaders feel their cybersecurity risks are increasing.
Impact of Cyber Threats on Individuals and Businesses
Cyber threats can have devastating effects on both individuals and businesses:
- Financial Loss: Cyber attacks can lead to significant financial losses due to fraud, theft, and ransomware payments.
- Data Breaches: Unauthorized access to sensitive data can result in identity theft, legal repercussions, and loss of trust.
- Operational Disruption: Attacks like DDoS can disrupt business operations, leading to downtime and productivity loss.
How DePIN Networks Enhance Security
Decentralization and Its Benefits for Security
Decentralization is a core principle of DePIN networks, providing several security benefits:
- Reduced Single Points of Failure: By distributing data and control across multiple nodes, DePIN networks eliminate single points of failure, making it harder for attackers to compromise the entire system.
- Increased Resilience: Decentralized networks are more resilient to attacks, as the failure of one node does not affect the entire network.
Role of Cryptography in DePIN Networks
Cryptography plays a crucial role in DePIN networks, ensuring data security and privacy:
- Encryption: Data is encrypted both in transit and at rest, preventing unauthorized access.
- Digital Signatures: Cryptographic signatures ensure the authenticity and integrity of data, preventing tampering.
Decentralized Storage and Data Redundancy
DePIN networks use decentralized storage solutions, providing several advantages:
- Data Redundancy: Data is replicated across multiple nodes, ensuring that it remains accessible even if some nodes fail.
- Enhanced Privacy: Decentralized storage reduces the risk of data breaches, as attackers would need to compromise multiple nodes to access sensitive information.
Investing in DePIN networks can significantly enhance your cybersecurity posture. Explore the benefits of DePIN technology and consider integrating it into your security strategy.
Mechanisms of Protection in DePIN Networks
Data Encryption and Secure Communication
DePIN networks employ robust encryption techniques to protect data:
- End-to-End Encryption: Data is encrypted from the sender to the receiver, ensuring that it cannot be intercepted or tampered with during transmission.
- Secure Communication Channels: Encrypted communication channels protect data from eavesdropping and interception.
Distributed Ledger Technology and Immutability
Blockchain technology is a fundamental component of DePIN networks:
- Immutable Records: Once data is recorded on the blockchain, it cannot be altered or deleted, ensuring data integrity.
- Transparent and Verifiable: Blockchain provides a transparent and verifiable record of all transactions, enhancing trust and accountability.
Smart Contracts and Automated Security Protocols
Smart contracts are self-executing contracts with the terms of the agreement directly written into code:
- Automated Security: Smart contracts automate security protocols, ensuring that security measures are consistently applied.
- Reduced Human Error: Automation reduces the risk of human error, which can often lead to security vulnerabilities.
Case Studies: DePIN Networks in Action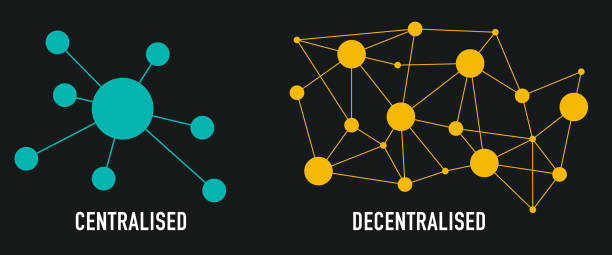
Real-World Examples of DePIN Networks Preventing Cyber Attacks
Several real-world examples demonstrate the effectiveness of DePIN networks in preventing cyber attacks:
- Secure Communication Platforms: Decentralized messaging platforms like Signal use end-to-end encryption to protect user data from interception.
- Decentralized Finance (DePIN): DePIN platforms leverage smart contracts to automate financial transactions, reducing the risk of fraud and ensuring transparency.
Success Stories of Businesses and Organizations Using DePIN for Enhanced Security
Businesses and organizations across various industries have successfully implemented DePIN networks for enhanced security:
- Healthcare: Decentralized health records ensure patient data privacy and security, preventing unauthorized access and data breaches.
- Supply Chain Management: Blockchain-based supply chain solutions enhance transparency and traceability, reducing the risk of fraud and counterfeit products.
Challenges and Limitations
Current Challenges in DePIN Implementation
Despite its many advantages, DePIN networks face several challenges:
- Scalability: As the number of nodes increases, maintaining network performance and efficiency can be challenging.
- Interoperability: Ensuring compatibility between different DePIN networks and traditional systems can be complex.
Potential Vulnerabilities and How They Are Addressed
While DePIN networks offer robust security, potential vulnerabilities exist:
- Consensus Mechanisms: Some consensus mechanisms may be susceptible to attacks, such as 51% attacks in proof-of-work systems.
- Node Compromise: If a significant number of nodes are compromised, the security of the entire network can be at risk.
Balancing Decentralization and Usability
Achieving a balance between decentralization and usability is crucial:
- User Experience: Ensuring a seamless user experience while maintaining high security can be challenging.
- Adoption Barriers: Technical complexity and lack of awareness can hinder the widespread adoption of DePIN networks.
Future Developments in DePIN Security
Emerging Technologies and Innovations in DePIN
The future of DePIN networks is promising, with several emerging technologies and innovations:
- Quantum-Resistant Cryptography: Developing cryptographic algorithms that are resistant to quantum computing threats.
- Zero-Knowledge Proofs: Enhancing privacy by allowing transactions to be verified without revealing sensitive information.
Predictions for the Future of DePIN and Cybersecurity
The future of DePIN networks and cybersecurity is intertwined:
- Increased Adoption: As awareness grows, more businesses and individuals will adopt DePIN networks for enhanced security.
- Regulatory Frameworks: Governments and regulatory bodies will develop frameworks to support and govern DePIN networks.
How Businesses Can Prepare for Future Cyber Threats
Businesses can take several steps to prepare for future cyber threats:
- Invest in DePIN Networks: Adopting DePIN networks can provide robust protection against emerging cyber threats.
- Continuous Monitoring and Updates: Regularly monitoring and updating security protocols to stay ahead of threats.
Conclusion
Recap of Key Points
DePIN networks offer a revolutionary approach to cybersecurity by leveraging decentralization, cryptography, and blockchain technology. They provide enhanced security features, robust protection mechanisms, and resilience against cyber threats.
The Importance of Adopting DePIN Networks for Cybersecurity
As cyber threats continue to evolve, adopting DePIN networks is crucial for businesses and individuals seeking to protect their data and ensure privacy.
Final Thoughts on the Role of DePIN in Protecting Against Cyber Threats
DePIN networks represent the future of cybersecurity, offering a promising solution to the growing cyber threat landscape. By embracing DePIN technology, we can create a more secure and resilient digital world.

 China
China Russia
Russia India
India